
Protecting your business from cyber threats starts with mastering the fundamentals. According to IBM's 2023 Cost Of A Data Breach Report, an alarming 82% of data breaches involved cloud-stored information, and most...
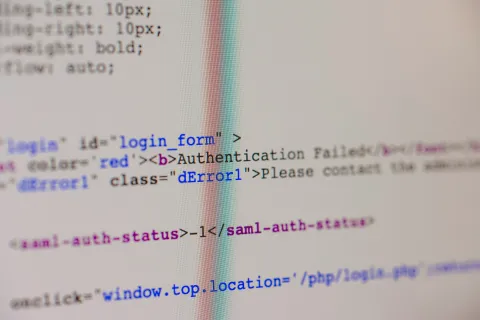
Why Multi-Factor Authentication Fails Multi-factor authentication (MFA) is a critical layer of defense in the fight against increasingly complex cyber threats. It's designed to prevent unauthorized access,...

Important Notice: Microsoft will officially end support for Windows 10 on October 14, 2025. Although your Windows 10 PC will continue to function after this date, Microsoft will stop providing essential services like...

Microsoft Sets End-of-Life for Windows 10: What It Means for Businesses and IT Planning Windows 10 has been the trusted foundation for business computing since its release in 2015. But Microsoft has announced...

The buzz around artificial intelligence (AI) is undeniable—and for good reason. Innovative tools like ChatGPT, Google Gemini, and Microsoft Copilot are revolutionizing how businesses operate. From generating...

The Real Cost of IT Downtime: Business Implications Key Takeaways The cost of IT downtime includes productivity loss, revenue impact, client dissatisfaction, and emergency recovery expenses....

While you and your team return refreshed from vacation, remember that cybercriminals never pause their attacks. Research from ProofPoint and Check Point reveals a notable surge in phishing scams during the summer...

Discover the Benefits of Managed IT Services Key Takeaways Subpar IT leads to recurring operational issues that affect productivity and client satisfaction Downtime has real financial...

Think cyberattacks only target large corporations? Think again. Small businesses have become prime targets for cybercriminals due to their often weaker defenses and higher likelihood to pay ransoms. Unlike Fortune...

Read the rest of his inspiring story on how TechSage Solutions became the business it is today.

The Compliance Formula simplifies complex compliance challenges, equipping businesses to achieve CMMC certification and protect against costly cyber threats. Written by top IT leaders, this book is essential for organizations seeking to win Department of Defense contracts, enhance security, and avoid the financial and legal risks of non-compliance.
